The Patelco data breach has garnered negative reviews and raised concerns about its legitimacy. This article provides an objective analysis of the incident, examining its scope, impact on affected customers, timeline, and causes.
It also offers practical advice on protecting oneself after a breach and emphasizes the importance of data privacy for businesses.
Additionally, the article discusses building trust through transparency and cybersecurity insurance, highlighting the need for continuous improvement and vigilance in cybersecurity measures.
This comprehensive analysis aims to inform and empower individuals and businesses alike.
Table of Contents
The Scope and Impact of the Breach
The breach’s scope and impact on Patelco Credit Union’s customers were far-reaching and devastating, with potentially thousands of individuals’ sensitive personal and financial information being exposed to hackers. The breach resulted in serious legal consequences for Patelco, as the failure to safeguard customer data violated privacy laws and regulations.
Additionally, the long-term financial impact on affected individuals cannot be understated. Victims may face significant challenges in undoing the damages caused by the breach, including the risk of identity theft and fraudulent account openings. This breach has also raised concerns about the security of current accounts and cards, as resourceful criminals armed with stolen financial data could target victims.
Furthermore, affected individuals will likely experience wasted time monitoring statements, reports, and accounts for suspicious activity or fraud losses. The breach highlights the need for organizations to prioritize data privacy and implement robust security measures to protect their customers’ sensitive information.
Timeline and Causes of the Breach
A timeline of the Patelco data breach reveals the sequence of events and the causes that led to the unauthorized access of customer information.
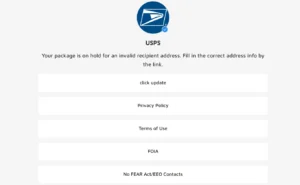
The breach began on March 7, 2021, when cybercriminals launched a sophisticated phishing attack targeting Patelco employees via email, tricking them into providing login credentials.
Over the following weeks, the hackers explored internal systems undetected and located the valuable customer database containing personal data.
The breach went unnoticed due to a lack of network monitoring and outdated software/systems that allowed known vulnerabilities to be exploited.
Additionally, the absence of proper segmentation made it easy for thieves to steal sensitive customer records.
These factors, including the consequences of the phishing attack, highlight the critical need for robust security measures and continuous monitoring to prevent unauthorized access to customer information.
Patelco Data Breach: Protecting Yourself After a Breach
Fortunately, there are several proactive steps you can take to protect yourself after a data breach:
- Place a credit freeze: Contact the three major credit bureaus (Equifax, Experian, and TransUnion) to freeze your credit. This will prevent new accounts from being opened using your social security number.
- Regularly review financial statements: Take the time to carefully review your financial statements for any unexpected charges or transfers. If you notice any fraudulent activity, report it immediately to your financial institution.
- Consider credit monitoring services: Signing up for a credit monitoring service can help you actively scan public records and the dark web for signs of misuse. These services can provide you with alerts if any suspicious activity is detected.
- Monitor credit reports: Visit AnnualCreditReport.com to monitor your credit reports directly. Look out for any irregular inquiries or accounts that you do not recognize. Report any discrepancies immediately to the credit bureaus.
Importance of Data Privacy for Businesses
Data privacy is an imperative concern for businesses as it encompasses more than just financial loss and reputation damage. Mishandling sensitive customer information can have severe consequences for businesses.
In today’s digital age, data privacy regulations are becoming more stringent, and companies must comply with these regulations to avoid legal penalties and fines. Additionally, mishandling customer information can lead to trust erosion, which can result in a loss of customers and damage to the brand’s reputation.
Customers expect businesses to protect their personal data and trust that it will be handled securely. Failure to do so can lead to a loss of customer loyalty and potential legal action. Therefore, it is crucial for businesses to prioritize data privacy and take proactive measures to protect customer information.
Building Trust Through Transparency and Cybersecurity Insurance
By prioritizing transparency and investing in cybersecurity insurance, businesses can build trust and enhance their ability to handle data breaches effectively.
Here are some best practices for transparency in data breaches and the benefits of cybersecurity insurance:
- Open and timely communication: Customers appreciate businesses that are open and transparent about data breaches. Promptly notifying affected individuals and providing regular updates can help minimize the negative impact of the breach.
- Enterprise-wide security culture: Building a culture of security throughout the organization is crucial for effective data protection. This involves training employees on cybersecurity best practices and ensuring they understand their role in safeguarding customer data.
- Cybersecurity insurance: Investing in cybersecurity insurance can provide financial support in the event of a breach. It helps mitigate the potential lawsuits and damages that may arise from the incident. Insurance also demonstrates a commitment to protecting customer data and adds an extra layer of protection.
- Learning from past mistakes: Examining previous breaches, such as the Patelco breach, can help organizations strengthen their protection and response strategies. By learning from failures and continuously improving security measures, businesses can stay ahead of evolving cyber threats and better serve their customers.
Continuous Improvement and Vigilance in Cybersecurity
Continuous improvement and vigilance are essential in maintaining robust cybersecurity defenses against evolving cyber threats. As cybercriminals become more sophisticated and creative in their attacks, organizations must engage in continuous learning to stay ahead. This involves staying updated on the latest cybersecurity trends, vulnerabilities, and best practices.
Implementing proactive measures, such as regularly patching software and systems, using strong passwords, and enabling two-factor authentication, can significantly reduce vulnerabilities. It is crucial for businesses to invest in people, processes, and technology to enhance their security posture.
Complacency is a major threat to digital security, and organizations must learn from both successes and failures in security to make ongoing progress. By embracing a culture of continuous improvement and vigilance, businesses can better protect themselves and their customers’ sensitive data.
Conclusion
In conclusion, the Patelco data breach has revealed the need for businesses to prioritize data privacy and invest in robust cybersecurity measures.
The breach has had a significant impact on affected customers, highlighting the importance of protecting personal information.
By adopting transparent practices and considering cybersecurity insurance as a risk management tool, organizations can build trust with their customers.
Continuous improvement and vigilance in cybersecurity are crucial for safeguarding sensitive data and ensuring the security of individuals and businesses.
Also Read
Is Store-News@Amazon Legit? Amazon Gift Card Email Scam
Google Play Gift Card Amazon Scam Email Explained
Amazon Hotels.Com Gift Card Scam Email Exposed
Also Read
Amazon Mastercard Gift Card Scam Email Exposed
Amazon Gift Card Order Scam Email: Don’t Fall Victim
Amazon Email Gift Card Purchase Scam Email
Also Read
Buynutriblade. Com Review: NutriBlade Knives Slice
Fusionartai Com Reviews: Explore Its Features & Legitimacy
Is Store News Amazon Com a Legit Email? Explained
Also Read