Moroccan Earthquake Whatsapp Scam – In recent days, a viral warning has circulated on WhatsApp, raising concerns about a supposed Morocco Earthquake Seismic Wave Card hack.
This article aims to provide clarity and debunk this hoax, highlighting the lack of evidence for the existence of such a card.
While it is important to remain cautious with digital files, it is crucial to note that user action is required for image-based malware.
By practicing good internet hygiene and adopting preventive measures, individuals can reduce the risk of falling victim to such threats.
Table of Contents
Moroccan Earthquake Whatsapp Scam: A False Threat of the Seismic Wave Card
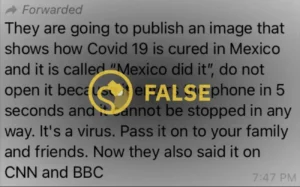
The viral hoax surrounding the Seismic Wave Card falsely threatens smartphone users with a hack that can compromise their personal data and disrupt communication networks. This hoax has spread rapidly through social media platforms, highlighting the role of social media in the dissemination of hoaxes.
The psychological impact of viral threats is significant, as it creates fear and anxiety among smartphone users, leading them to take unnecessary precautions and share the information with their family and friends.
The spread of such hoaxes demonstrates the power of social media in influencing public perception and behavior. It is important for users to critically evaluate the information they receive and verify its authenticity before sharing it further.
Understanding the Reality: No Evidence of a Seismic Wave Card
There is no evidence or proof to support the existence of a Seismic Wave Card as claimed in the viral warning on WhatsApp.
The hoax, which warns users about a card containing photos of the recent Morocco earthquake, urges them not to open the file as it will hack their phones in 10 seconds.
This is an example of a viral hoax that preys on people’s fears and lack of media literacy in the digital age.
Understanding the psychology behind these hoaxes is crucial in combating their spread.
Media literacy, which involves critical thinking and evaluating the credibility of information, is essential in navigating the digital landscape.
Unmasking Image-Based Malware: How It Works and What to Know
Digital steganography allows for the covert embedding of malicious code within digital files, requiring user action to execute and potentially compromise the security of mobile devices. Unveiling the techniques used in image-based malware is essential to understand the psychology behind viral hoaxes.
By exploring the psychology behind viral hoaxes, we can gain insight into the motivations of those who create and spread such malicious content. Additionally, understanding the techniques used in image-based malware can help users recognize and avoid potential threats.
Some techniques used in image-based malware include hiding malicious code within images, exploiting vulnerabilities in image-processing software, and using social engineering tactics to trick users into downloading infected files.
Awareness of these techniques can empower users to protect themselves from image-based malware attacks and maintain the security of their mobile devices.
Debunking the 10-Second Hack: User Action Required for Malicious Code
User action is essential for the execution of malicious code embedded in image-based malware, debunking the claim that a 10-second hack can occur without any interaction from the user.
Digital steganography plays a significant role in image-based malware, allowing the hiding of secret messages and data within digital files.
However, it is important to note that image-based malware cannot hack smartphones on its own. It requires user action, such as downloading or installing from unknown websites, for the malicious code to execute.
Practicing good internet hygiene, such as avoiding downloads from unknown sources, can significantly reduce the risk of infection.
Therefore, it is crucial to debunk myths about smartphone hacking and raise awareness about the importance of user actions in preventing malware attacks.
Potential Impact: The Dangers and Consequences of the Hack
The hack can have severe consequences, including:
- Unauthorized access to personal data
- Compromised privacy and security
- Identity theft
- Financial fraud
- Disruption of communication networks
- Financial losses for individuals and businesses
These consequences can lead to various negative outcomes. Additionally, there are other aspects to consider:
Legal implications: Potential legal consequences for individuals involved in spreading hoaxes and malicious content.
Psychological impact: Falling victim to a hack can have significant psychological effects. This includes feelings of violation, fear, and anxiety. It can also shatter one’s sense of security and trust in technology.
Ways to mitigate emotional distress: Seeking support from friends, family, or professionals can help individuals cope with the psychological impact of a hack.
Engaging in self-care activities, such as exercise, meditation, and hobbies, can also promote emotional well-being. Educating oneself about cybersecurity best practices and implementing preventive measures can provide a sense of empowerment and security.
Preventive Measures: Strengthening Security to Avoid Falling Victim
To avoid falling victim to unauthorized access, compromised privacy, identity theft, financial fraud, disruption of communication networks, and financial losses, it is essential to strengthen security measures and implement preventive actions.
One effective measure is strengthening encryption protocols. By enhancing the encryption algorithms and keys used to secure sensitive data, the risk of unauthorized access and data breaches can be significantly reduced.
Additionally, global collaboration plays a crucial role in improving security. Sharing information, best practices, and threat intelligence across international boundaries can help identify vulnerabilities and develop more robust security solutions.
It is vital for governments, businesses, and individuals to work together in addressing the ever-evolving threats and ensuring a safer digital environment.
Future Directions: Advancements in Mobile Phone Technologies and Research
Advancements in mobile phone technologies and ongoing research are focusing on strengthening security measures and developing more secure encryption techniques to prevent unauthorized access and protect sensitive data. Collaborative efforts in cybersecurity are driving these advancements, with researchers and industry professionals working together to enhance the security of mobile devices.
Some key developments in this area include:
- Implementation of stronger encryption algorithms: Researchers are exploring advanced encryption techniques to ensure that data transmitted and stored on mobile phones remains secure and inaccessible to unauthorized individuals.
- Integration of biometric authentication: Mobile phone manufacturers are incorporating biometric authentication methods, such as fingerprint or facial recognition, to provide an additional layer of security and prevent unauthorized access.
- Enhanced security protocols: Ongoing research is focused on developing robust security protocols that can detect and prevent sophisticated hacking attempts, ensuring the integrity and confidentiality of user data.
These advancements in encryption and collaborative efforts in cybersecurity are crucial in safeguarding mobile phone users’ personal information and providing them with a sense of belonging to a secure digital community.
Conclusion – Moroccan Earthquake Whatsapp Scam
In conclusion, the viral warning about the Morocco Earthquake Seismic Wave Card hack is a hoax with no evidence to support its existence.
Image-based malware requires user action to be activated, emphasizing the importance of good internet hygiene and cautious behavior.
While the potential impact of such a hack can be dangerous, preventive measures can significantly reduce the risk of falling victim.
Ongoing research and advancements in mobile phone security aim to enhance the protection of users and their devices.
Also Read
Is Zenatime Scam or Legit? Zenatime.Com Reviews
Conlarlys Bra Reviews – Legit Or Scam? Unveiling The Truth
Swim Recruiting Scam Exposed – Don’t Fall for Fake Job Scams
Also Read
Mason Blake Recruitment Whatsapp Scam – Don’t Fall Victim
Elite Healthcare & Wellness Scam or Legit? Don’t Be Fooled
Pinreadca Com Scam or Legit? Don’t Fall Victim
Also Read
Floresta Reviews – Is Floresta Legit or a Scam? Don’t Fall It
Ccdrrf Com Scam or Legit? – Ccdrrf.Com Exposed
Roalert.com Reviews – Is Roalert.com Legit or a Scam?
Also Read
Meaifeer Reviews – Is Meaifeer Legit or a Scam?
Libiyi Drill Bit Reviews – Is Libiyi Drill Bit Legit or a Scam?
Smartwool Sale Scam or Legit? Smartwool.Sale Exposed
Also Read